Zero Trust Security Solutions
Protecting organizations from data breaches starts with identity
Request demoSecure support for employees working remotely

Network and application security is becoming increasingly complex, and SpeedBox can help telecommuting employees stay productive anywhere, anytime by providing zero-trust network access to all enterprise applications, effectively preventing security threats to your network.
Identity and access management can be simply defined as ensuring that the right people access the right resources for the right reasons at the right time. This network-centric security scheme works well when employees are in the office, but today, employees Work in many different locations. IT departments cannot guarantee the security of such networks, and organizations cannot manage devices. These reasons can lead to some serious security breaches, and a single unmanaged device infected with malware can put your entire network at risk. Once an unauthorized user gains access, it opens the door to lateral movement.
To solve the data leakage risks faced by enterprises in an integrated way, and establish a whole-domain data security and operation governance system for enterprises.
What is the solution?
The SpeedBox solution supports organizations that require authentication for secure access at scale. While an organization's web services, data and application access needs will vary depending on different user requirements, SpeedBox provides secure access for all through three key components:
- Use strong authentication and bind user identities to user roles to authorize access to appropriate resources.
- Manage the digital certificates used to authenticate the identity of domain owners such as websites, companies, individual users or devices.
- Use the SSO function to reduce user logins. Users only need to log in once and can access the allowed resources with a single click.

Working Principle
With the continuous digital transformation of enterprises, the normalisation of telecommuting, and a large number of enterprise businesses going to the cloud, the network boundaries of enterprises are gradually blurring and the traditional boundary-based security framework is facing increasing challenges. It is difficult to effectively meet the current security requirements of enterprises by constructing trust relationships with traditional internal and external network boundaries.
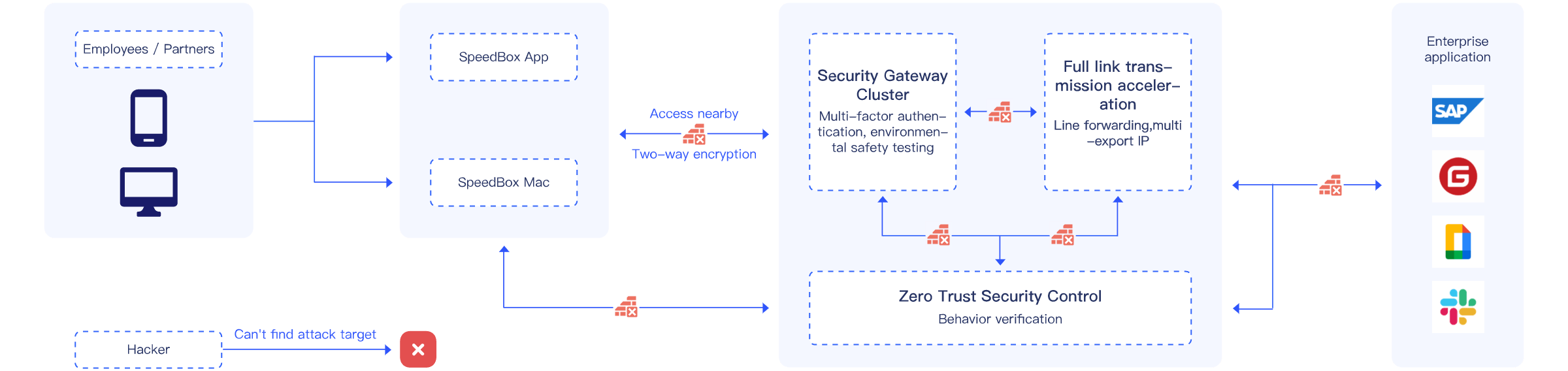


Key Function

Secure access to multiple enterprise applications
Go beyond traditional single sign-on (sso) with adaptive access capabilities

Multi-factor authentication
Prevent hackers from using weak or stolen passwords to gain network access

Terminal environment security detection
Continuous monitoring of the user's environment to ensure environmental safety

Using VPN Alternatives to Meet the Needs of Remote Workers
Taking a Zero Trust Approach to Preventing Network-Level Attacks
How can you benefit from SpeedBox?
Cut Costs
Centralised identity storage across the organisation, user resource deployment and authentication, and troubleshooting reduce operational costs.
Business Agility
Powerful authentication improves compliance, reduces the risk of data leakage, and allows BOYD and cloud applications.
Increased productivity and safety
SSO provides the best user experience, reducing login fatigue and the risk of impacting logins.